- Technology
- SEE MORE
- classical
- general
- talk
- News
- Family
- Bürgerfunk
- pop
- Islam
- soul
- jazz
- Comedy
- humor
- wissenschaft
- opera
- baroque
- gesellschaft
- theater
- Local
- alternative
- electro
- rock
- rap
- lifestyle
- Music
- como
- RNE
- ballads
- greek
- Buddhism
- deportes
- christian
- piano
- djs
- Dance
- dutch
- flamenco
- social
- hope
- christian rock
- academia
- afrique
- Business
- musique
- ελληνική-μουσική
- religion
- World radio
- Zarzuela
- travel
- World
- NFL
- media
- Art
- public
- Sports
- Gospel
- st.
- baptist
- Leisure
- Kids & Family
- musical
- club
- Culture
- Health & Fitness
- True Crime
- Fiction
- children
- Society & Culture
- TV & Film
- gold
- kunst
- música
- gay
- Natural
- a
- francais
- bach
- economics
- kultur
- evangelical
- tech
- Opinion
- Government
- gaming
- College
- technik
- History
- Jesus
- Health
- movies
- radio
- services
- Church
- podcast
- Education
- international
- Transportation
- Other
- kids
- podcasts
- philadelphia
- Noticias
- love
- sport
- Salud
- film
- and
- 4chan
- Disco
- Stories
- fashion
- Arts
- interviews
- hardstyle
- entertainment
- humour
- medieval
- literature
- alma
- Cultura
- video
- TV
- Science
- en

Unsolicited Response Podcast
Dale Peterson interviews the innovators in ICS / SCADA cyber security as well as the top talent in related fields. It is the podcast for those who want more information similar to what is presented at the annual S4 event each January in Miami South Beach.Pwn2Own Miami
Published: Jan. 26, 2021, 1 p.m.Duration: 53 minutes 29 seconds
Listed in: Technology
Are Your ICS Security Patching Plans Realistic?
Published: Jan. 22, 2021, 2:46 a.m.Duration: 4 minutes 6 seconds
Listed in: Technology
Is The Normalized, Taxonomized Approach In A SIEM Doomed To Fail
Published: Jan. 19, 2021, noonDuration: 40 minutes 22 seconds
Listed in: Technology
How To Be An OT Visionary
Published: Jan. 14, 2021, 10:45 p.m.Duration: 4 minutes 3 seconds
Listed in: Technology
ICS Breaches Will Happen
Published: Jan. 7, 2021, 8 a.m.Duration: 6 minutes 26 seconds
Listed in: Technology
December: ICS Security Month In Review
Published: Jan. 6, 2021, 7:30 a.m.Duration: 43 minutes 24 seconds
Topics:
- The Solarwinds hack
- Dragos raising $110M in venture funding
- The minimal number and damage from cyber attacks on ICS in 2020
Tweet Me! @digitalbond
Friday Newsletter: https://mailchi.mp/f53b1c8c2da0/friday
-->
Listed in: Technology
2020 Predictions: Right, Wrong and Pending
Published: Dec. 31, 2020, 9 a.m.Duration: 8 minutes 43 seconds
Listed in: Technology
ICS Detection Market Analysis - Part 2
Published: Dec. 15, 2020, 2 p.m.Duration: 11 minutes 58 seconds
Listed in: Technology
Weekly Article: ICS Detection Market Analysis - Part 1
Published: Dec. 10, 2020, 2 p.m.Duration: 12 minutes 5 seconds
Listed in: Technology
November: ICS Security Month In Review
Published: Nov. 30, 2020, 10:26 p.m.Duration: 55 minutes 53 seconds
Listed in: Technology
Impact to ICS Security Effort with Dir. Krebs Firing
Published: Nov. 23, 2020, 1 p.m.Duration: 41 minutes 51 seconds
Listed in: Technology
October: ICS Security Month In Review
Published: Nov. 2, 2020, 1:30 p.m.Duration: 46 minutes 13 seconds
Top Stories
1. Six Sandworm attackers from Russia charged. Why was this done now and what does it accomplish?
2. More ICS vendors announced security services (ABB and Siemens). Will this be a good business? Is it good for asset owners?
3. ICS security vendors are creating risk metrics for cyber assets and zones (Claroty and ID announced). How should asset owners view these metrics?
Plus Jason has a Win and Prediction, and I give my Win, Fail and Prediction for October.
Links
Jason Nations / Selena Larson S4x20 video - Understanding Our Adversaries
Thomas Rid's Active Measures book
ICS-Patch Decision Tree ... What To Patch When?
Finite State web page and Unsolicited Response episode
-->Listed in: Technology
September: ICS Security Month In Review
Published: Oct. 6, 2020, 9:31 p.m.Duration: 26 minutes 49 seconds
This month's stories include:
- S4x21's cancellation and S4x22 dates
- (7:01) Ransomware in ICS
- (12:30) SCIDMark and other ICS cyber incident databases
- (16:50) Is the Airgap myth still believed by asset owners?
- (21:51) Wins, Fails and Predication
This is a solosode, as my planned guest got sick (not Covid). And I also start the podcast with some information on S4x21's cancellation and S4x22.
Links
German death due to ransomware article
Sanjay Chhillar ICS Security Myth Presentation
DoE program to create and evaluate Schneider Electric SBOM (CyTRICS)
DoE funding NRECA ICS Detection Tool
-->
Listed in: Technology
ATT&CK for ICS Evaluations
Published: Sept. 30, 2020, 6:28 p.m.Duration: 49 minutes 12 seconds
In this episode I talk with Otis Alexander of MITRE about ATT&CK for ICS Evaluations. We begin with a discussion on ATT&CK and the ICS version of ATT&CK. If you are familiar with this, skip to 17:09 where we begin our discussion on the upcoming evaluations.
MITRE has created a Triton type attack and will test companies abilities to detect the various elements of this created attack. Five companies have signed up to be tested, and hopefully more will step up to this challenge.
Otis and I get into the details on how the testing takes place, the scope of the testing, how the results will be reported out, the value of the results to asset owners, and more.
Links
-->
Listed in: Technology
Splunk OT Security Add-On
Published: Sept. 16, 2020, 12:30 p.m.Duration: 51 minutes 46 seconds
In this episode of the Unsolicited Response podcast I talk with Ed Albanese, the VP Internet of Things at Splunk about the OT Security Add-On.
This is a more detailed, technical episode as I try to dig into the features and benefits of the integration today and where it can be improved in the future. This includes:
- The additional OT fields in the Splunk Asset Framework
- The OT_Asset and OT_SW_Asset data models
- How the 29 OT search queries will work with integrations likely using different terms (such as different names for asset types) and the types of search queries currently supported.
- The value of having standardizations for some OT alerts/events sent to Splunk, such as "modify control logic". This support for standardized notables, as Splunk calls them, is not in the released Add-On but can be configured.
- How Splunk is tracking vulnerability management (currently no OT integration)
- And how Splunk is calculating the Risk Scores in the OT Security Posture Tab
Links
Splunk OT Security Add-On Announcement
Splunk OT Security Add-On Software Download Page
-->Listed in: Technology
What OT Can Learn From IT
Published: Sept. 2, 2020, noonDuration: 41 minutes 38 seconds
- OT doesn't really understand IT, and the similar, but not identical, requirements that mission critical IT has with OT.
- OT can actually learn a lot from IT.
So I wanted to discuss this with someone with significant experience in both OT and IT security. Lesley Carhart of Dragos was a great choice. Before Dragos she worked for Motorola and was involved with incident response for both OT and mission critical IT.
I talk and opine a bit more than normal in this episode because I have strong feelings on this topic.
Send any comments or suggestions to s4@digitalbond.com, and subscribe if you haven't already.
Links
Lesley Carhart on Twitter: @hacksforpancakes
Lesley Carhart personal website
Lesley's DerbyCon session: Confessions of an IT / OT Marriage Counselor
-->Listed in: Technology
DHS CISA's New Strategy
Published: Aug. 18, 2020, noonDuration: 46 minutes 11 seconds
Listed in: Technology
July - ICS Security Month In Review
Published: Aug. 4, 2020, noonDuration: 53 minutes 2 seconds
Listed in: Technology
Peter Singer - Author of Burn In: A Novel About The Real Robotic Revolution
Published: July 7, 2020, noonDuration: 48 minutes 25 seconds
Listed in: Technology
June - ICS Security Month In Review
Published: July 2, 2020, noonDuration: 57 minutes 9 seconds
Listed in: Technology
Building & Using Digital Twins
Published: June 25, 2020, noonDuration: 42 minutes 39 seconds
Listed in: Technology
Matt Wyckhouse: Testing ICS Firmware Security & Supply Chains
Published: June 16, 2020, 3:45 p.m.Duration: 50 minutes 49 seconds
Listed in: Technology
May: ICS Security Month In Review
Published: June 5, 2020, 2:54 a.m.Duration: 56 minutes 17 seconds
Listed in: Technology
COVID-19 Impact In ICS Security
Published: May 27, 2020, 10 p.m.Duration: 24 minutes 9 seconds
Listed in: Technology
Interview with Inventor & Legend Ed Schweitzer
Published: April 21, 2020, 3:53 a.m.Duration: 34 minutes 43 seconds
Listed in: Technology
Interview with Bryan Owen of OSIsoft
Published: April 14, 2020, 5:25 p.m.Duration: 42 minutes 40 seconds
Listed in: Technology
Tenable's OT Strategy with Marty Edwards
Published: April 7, 2020, 4:39 p.m.Duration: 44 minutes 12 seconds
Listed in: Technology
Board of Directors Role in ICS Security with Thomas Parenty
Published: March 31, 2020, 5:39 p.m.Duration: 53 minutes 35 seconds
Listed in: Technology
ICS Threat Intel with Sergio Caltagirone
Published: March 23, 2020, 9:52 p.m.Duration: 46 minutes 20 seconds
Listed in: Technology
An Interview with Andy Greenberg - Author of Sandworm
Published: March 18, 2020, 8:27 p.m.Duration: 36 minutes 47 seconds
Listed in: Technology
Kelly Jackson Higgins Interviews Dale
Published: March 4, 2020, 1:42 a.m.Duration: 32 minutes 24 seconds
Listed in: Technology
The Cabana Sessions
Published: Feb. 25, 2020, 5:46 p.m.Duration: 23 minutes 47 seconds
Listed in: Technology
Megan Samford on ICS4ICS
Published: Feb. 12, 2020, 8:34 p.m.Duration: 26 minutes 6 seconds
Listed in: Technology
Interview with DHS CISA Director Chris Krebs
Published: Feb. 5, 2020, 7:52 p.m.Duration: 31 minutes 52 seconds
Listed in: Technology
An Interview with Marina Krotofil
Published: Oct. 29, 2019, 5:06 p.m.Duration: 51 minutes 57 seconds
Listed in: Technology
Sean McBride on ICS Security Education and Degree Programs
Published: Oct. 17, 2019, 11:46 p.m.Duration: 45 minutes 8 seconds
Listed in: Technology
An Interview with Patrick Miller
Published: Oct. 7, 2019, 12:49 a.m.Duration: 51 minutes 48 seconds
Listed in: Technology
S4x19 Closing Panel
Published: Aug. 14, 2019, 6:08 a.m.Duration: 37 minutes 57 seconds
The S4 Closing Panel is always a candid discussion on where the community is in securing ICS, where we are succeeding and where need to do better. This year I was joined by Rob Lee of Dragos and Zach Tudor of INL.
Also note that the S4x20 Call For Presentations closes on Thursday (August 15).
Links
Sponsors
This episode was sponsored by aeSolutions. aeSolutions is an engineering and consulting company specializing in process safety and industrial cybersecurity. aeSolutions has pioneered the CyberPHA methodology which is a proven method to assess industrial control system (ICS) cybersecurity risk leveraging well established process safety techniques.
This episode was sponsored by CyberX. Founded by military cyber experts with nation-state expertise defending critical infrastructure, CyberX has developed an end-to-end platform for continuous ICS threat monitoring and risk mitigation. Check out the 2019 CyberX Global ICS and IIoT Risk Report, the CyberX report on the NIS Directive, and my podcast from last year on the report with Phil Neray.
-->Listed in: Technology
Rockwell Automation Cybersecurity
Published: July 17, 2019, 3:19 a.m.Duration: 1 hour 8 minutes 41 seconds
In this episode of the Unsolicited Response Podcast I interview Megan Samford and Rick Cherney of Rockwell Automation.
We cover two main topics. First, we discuss how they are dealing with vulnerabilities reported to them by researchers and other means. We focus on how this has progressed over the years as well as how vendors could provide more useful vulnerability and remediation information to their customers.
Second we discuss the Rockwell Automation getting past the Insecure By Design issue that has plagued the Level 1 / PLC devices. Most notably the signed firmware and ICS protocol security in CIP Security. We also delve into the challenges of getting CIP Security deployed in both green field and legacy systems.
I begin the podcast with a brief tribute to Mike Assante's unique skills and how they helped the ICS security effort. They pale in importance to the tributes of Mike as a father, friend and mentor, but nevertheless were impressive and hopefully some can pick up the load.
Links
- CIP Security Video from S4
- Rockwell Automation Security Home Page
- Rockwell Automation Industrial Security Advisory Index (Requires Account Registration)
- Factory Talk Policy Manager Getting Results Guide (CIP Security Configuration Software)
- S4x20 Call For Presentations
- Just three of the many Mike Assante tributes are an article on CSO from Aaron Turner, Rob Lee’s blog and a final message from Mike to the community.
Sponsors
This episode was sponsored by CyberX. Founded by military cyber experts with nation-state expertise defending critical infrastructure, CyberX has developed an end-to-end platform for continuous ICS threat monitoring and risk mitigation.
This episode was sponsored by aeSolutions. aeSolutions is an engineering and consulting company specializing in process safety and industrial cybersecurity. aeSolutions has pioneered the CyberPHA methodology which is a proven method to assess industrial control system (ICS) cybersecurity risk leveraging well established process safety techniques.
-->Listed in: Technology
Forescout's Strategy Post SecurityMatters Acquisition
Published: June 27, 2019, 8:05 p.m.Duration: 54 minutes 28 seconds
Forescout's acquisition of SecurityMatters for $113M in cash was the first major exit from the OT Detection Space (or broader passive monitoring market as you will hear in the podcast). I spoke with Brian Proctor about a number of issues including:
- What it was like moving from an asset owner to a vendor
- The best way for an asset owner to recruit or develop ICS security talent in this high demand environment
- His thoughts on the OT Detection and broader passive monitoring space (and my Endgame article)
- Forescout's strategy for the OT capabilities in their "platform" and the market in general
WARNING: If you are one who gets offended by commercial content in a presentation or podcast, perhaps you should skip this episode. When the primary topic is a company's strategy to address the market it is impossible to expect the guest to not promote their offerings. The answers to me questions almost required a response that would be considered promotional. I will write up my analysis of the Forescout strategy in the upcoming weeks.
Links
- Forescout's Website
- ICS Detection Endgame Article
- S4x20 Call For Presentations
- OnRamp Online Registration
Sponsors
This episode was sponsored by CyberX. Founded by military cyber experts with nation-state expertise defending critical infrastructure, CyberX has developed an end-to-end platform for continuous ICS threat monitoring and risk mitigation.
This episode was sponsored by aeSolutions. aeSolutions is an engineering and consulting company specializing in process safety and industrial cybersecurity. aeSolutions has pioneered the CyberPHA methodology which is a proven method to assess industrial control system (ICS) cybersecurity risk leveraging well established process safety techniques.
-->Listed in: Technology
An Interview With Jonathan Homer of DHS
Published: June 12, 2019, 2:56 p.m.Duration: 38 minutes 9 seconds
In this episode, I interview Jonathan Homer, the Chief of the Industrial Control Systems Group / Hunt and Incident Response Team at DHS.
We discuss:
- What changes will asset owners see with the creation of CISA organization in DHS?
- A detailed discussion of the metrics DHS will use to determine if they are successful / having an impact?
- Why or if DHS is competing with industry in many of their ICS security services.
- The CISA Strategic Risk Management Process and how it will prioritize ICS security related efforts based on critical functions and specific assets.
Links
- DHS CISA Critical Infrastructure Vulnerability Assessments
- DHS National Critical Functions and Risk Register
- S4x20 Call For Presentations
- OnRamp Online Registration
Sponsors
This episode was sponsored by CyberX. Founded by military cyber experts with nation-state expertise defending critical infrastructure, CyberX has developed an end-to-end platform for continuous ICS threat monitoring and risk mitigation.
This episode was sponsored by aeSolutions. aeSolutions is an engineering and consulting company specializing in process safety and industrial cybersecurity. aeSolutions has pioneered the CyberPHA methodology which is a proven method to assess industrial control system (ICS) cybersecurity risk leveraging well established process safety techniques.
-->Listed in: Technology
ICS Firewall Market & Scoring SW/FW
Published: June 3, 2019, 10:19 a.m.Duration: 1 hour 2 minutes 15 seconds
Listed in: Technology
Truth or Consequences?
Published: May 14, 2019, 11:09 p.m.Duration: 38 minutes 59 seconds
This recording is from a panel discussion on understanding and reducing the consequence side of the risk equation (risk = consequence * likelihood). Joining me in this discussion are:
- John Cusimano of aeSolutions and their CyberPHA
- Andy Bochman of INL and their Consequence Driven Cyber Informed Engineering (CCE)
The two gentleman begin by explaining their respective consequence based risk assessment and risk management, and the diagrams they refer to are below.
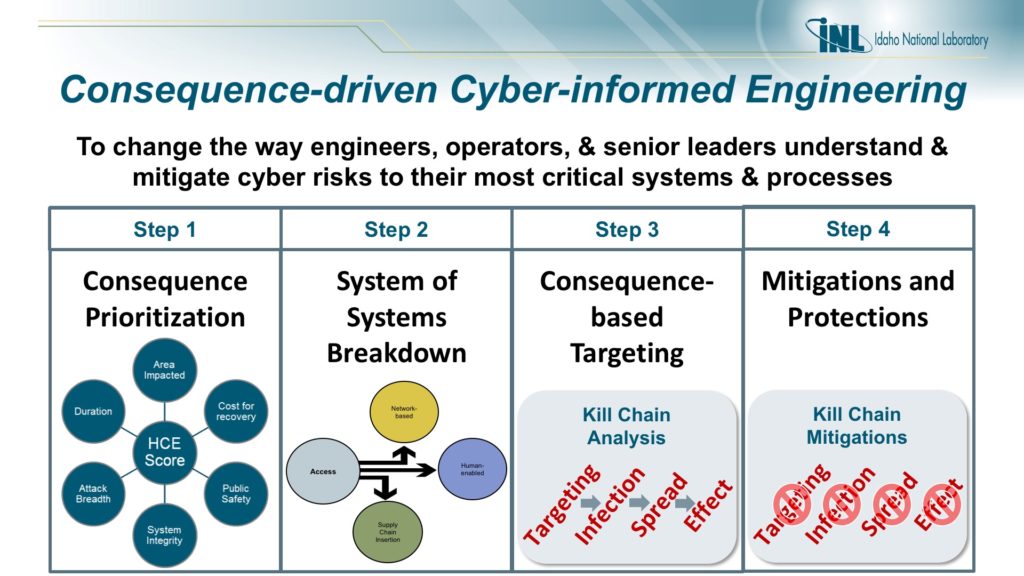 INL CCE Approach In One Slide
INL CCE Approach In One Slide
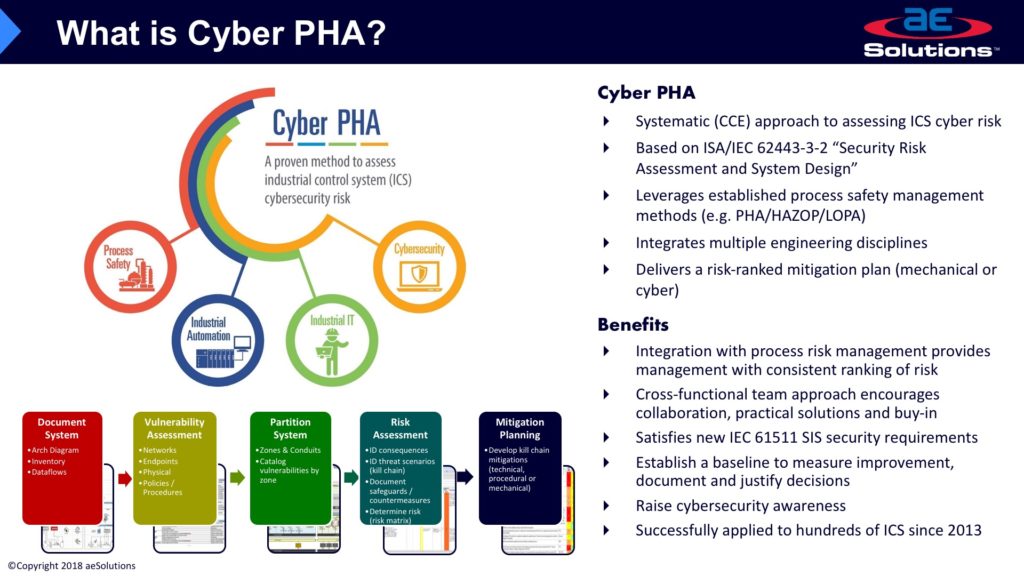 aeSolutions CyberPHA Approach In One Slide
aeSolutions CyberPHA Approach In One Slide
After the initial descriptions we discuss:
- how the two approaches are similar and different?
- how long it takes to perform a CCE or CyberPHA?
- what are some of the novel consequence reduction solutions?
- the difference between disruption and destruction as a consequence?
- will the CyberPHA be integrated into the PHA?
Links
This episode was sponsored by CyberX. Founded by military cyber experts with nation-state expertise defending critical infrastructure, CyberX has developed an end-to-end platform for continuous ICS threat monitoring and risk mitigation.
Check out the 2019 CyberX Global ICS and IIoT Risk Report, the CyberX report on the NIS Directive, and my podcast from last year on the report with Phil Neray.
-->Listed in: Technology
Maritime Cybersecurity
Published: April 2, 2019, 10:58 p.m.Duration: 52 minutes 40 seconds
In a recent article a researcher proclaimed it's "not hard for a hacker to capsize a ship at sea". This was quickly followed by the Viking Sky cruise ship having its engines shut off due to a sensor reading.
Not knowing much about maritime control systems I brought two experts from Moran Cyber on the podcast to discuss the issue: Captain Alex Soukhanov (a Master Mariner and Director at Moran Cyber) and Greg Villano (Senior Maritime Cybersecurity Engineeer at Moran Cyber). Both Alex and Greg have spent their careers on ships and now are working to secure the control systems that are becoming more essential every year.
Not knowing much about this sector, you hear the line of questioning that is used to begin to understand risk. It actually focuses more on impact and recovery than a list of specific security controls. It appears the maritime industry will face increasing challenges as they move away from ships that can continue to operate with manual operations.
-->Listed in: Technology
RSA Conference / ICS Village Report
Published: March 20, 2019, 11:56 p.m.Duration: 25 minutes 1 second
Listed in: Technology
An Interview With Robert Graham
Published: Feb. 28, 2019, 12:10 a.m.Duration: 41 minutes 40 seconds
Listed in: Technology
Is The Purdue Model Dead?
Published: Feb. 12, 2019, 1:13 a.m.Duration: 34 minutes 47 seconds
Listed in: Technology
4 Takeaways from 2018 ... And Kicking Off 2019 With My S4x19 Mini Keynote
Published: Jan. 29, 2019, 6:49 p.m.Duration: 25 minutes 41 seconds
Listed in: Technology
Neighborhood Keeper
Published: Nov. 8, 2018, 5:43 p.m.Duration: 1 hour 59 seconds
Listed in: Technology
Flawed ICS Mantras
Published: Oct. 18, 2018, 2:41 a.m.Duration: 21 minutes 41 seconds
Listed in: Technology
Ralph Langner on the ICS Security Product Market
Published: Sept. 27, 2018, 6:43 p.m.Duration: 1 hour 44 seconds
Listed in: Technology
Blake Sobczak on Electric Sector Cybersecurity
Published: Sept. 13, 2018, 5:05 a.m.Duration: 52 minutes 1 second
Listed in: Technology
CCE with Andy Bochman of INL
Published: July 18, 2018, 4:28 a.m.Duration: 1 hour 7 minutes 52 seconds
Listed in: Technology
Michael Assante Interview
Published: June 12, 2018, 9:19 p.m.Duration: 1 hour 9 minutes 47 seconds
Listed in: Technology
Cyber Hygiene?
Published: May 15, 2018, 1:37 p.m.Duration: 1 hour 1 minute 12 seconds
Listed in: Technology
What's Happening At ICS & IT Security Conferences
Published: May 9, 2018, 12:19 a.m.Duration: 57 minutes 55 seconds
Listed in: Technology
Press Coverage of ICS Security
Published: May 2, 2018, 6:41 a.m.Duration: 50 minutes 59 seconds
Listed in: Technology
Iatrogenics - Harm Done By The Healer
Published: April 5, 2018, 1:51 a.m.Duration: 41 minutes 18 seconds
Listed in: Technology
Enterprise SOC or IT SOC
Published: March 15, 2018, 11:44 a.m.Duration: 39 minutes 17 seconds
Listed in: Technology
ICS Detection Challenge Part 2
Published: March 7, 2018, 1 p.m.Duration: 55 minutes 42 seconds
Listed in: Technology
S4x18 ICS Detection Challenge Analysis
Published: Feb. 27, 2018, 11 a.m.Duration: 55 minutes 46 seconds
Listed in: Technology
Medical Sector Cybersecurity & Dense Vulnerabilities
Published: Feb. 20, 2018, 4:01 a.m.Duration: 57 minutes 35 seconds
Listed in: Technology
Dan Geer Interview at S4x18
Published: Feb. 1, 2018, 5:50 a.m.Duration: 40 minutes 14 seconds
Listed in: Technology
2018 Plans: Podcast, S4, Consulting & Your Career
Published: Jan. 2, 2018, 1 p.m.Duration: 13 minutes 46 seconds
Listed in: Technology
Threat and Detection Debate
Published: Dec. 13, 2017, 3:04 a.m.Duration: 53 minutes 34 seconds
Listed in: Technology
Next Generation Security Audit Files for ICS
Published: Dec. 1, 2017, 8:18 p.m.Duration: 49 minutes 17 seconds
Listed in: Technology
ICS Capture The Flag at S4x18
Published: Nov. 28, 2017, 6:39 a.m.Duration: 27 minutes 3 seconds
Listed in: Technology
Securing ICS Protocols
Published: Nov. 20, 2017, 6:23 p.m.Duration: 45 minutes 29 seconds
Listed in: Technology
The ICS Detection Challenge at S4x18
Published: Nov. 14, 2017, 6:34 a.m.Duration: 19 minutes 18 seconds
Listed in: Technology
Understanding & Interpreting ICS Security Statistics
Published: Nov. 2, 2017, 9:14 p.m.Duration: 48 minutes 25 seconds
Listed in: Technology
Kaspersky and Cyber Nationalism
Published: Oct. 4, 2017, 7:19 p.m.Duration: 34 minutes
Listed in: Technology
SCADA Apologist or SCADA Realist
Published: Sept. 20, 2017, 6:36 a.m.Duration: 37 minutes 21 seconds
Listed in: Technology
NERC CIP's Impact on Electric Sector Security
Published: Sept. 7, 2017, 2:49 a.m.Duration: 50 minutes 51 seconds
Listed in: Technology
State of Fuzzing ICS Protocols in 2017
Published: Aug. 23, 2017, 7:50 p.m.Duration: 34 minutes 33 seconds
Listed in: Technology
Interview with Steve Bitar of Exxon Mobil on Open Process Automation
Published: Aug. 15, 2017, 7:20 a.m.Duration: 41 minutes 58 seconds
Listed in: Technology
Selecting an IDS Detection Solution
Published: July 19, 2017, 6:42 p.m.Duration: 47 minutes 1 second
Listed in: Technology
Interview with Joel Langill, aka the SCADAhacker
Published: June 28, 2017, 10:41 p.m.Duration: 44 minutes 1 second
Listed in: Technology
John Matherly - The Creator of Shodan
Published: May 24, 2017, 3:33 a.m.Duration: 47 minutes 57 seconds
Listed in: Technology